Tutorials
Prior to version 6.0, iDefender relied on manual HIPS, which required properly configured rules to deliver optimal defense capabilities.
iDefender is different from traditional HIPS and instead uses a template-based rule model. Simply setting a few path parameters can complete the rule editing for a specific case.
Basic Rule
Here is an example of how to create a simple rule to block a process from executing. First, add a new rule and choose the Block Process Execution template. Then, just enter the details of the process you want to block. That's all it takes to set up process execution blocking.
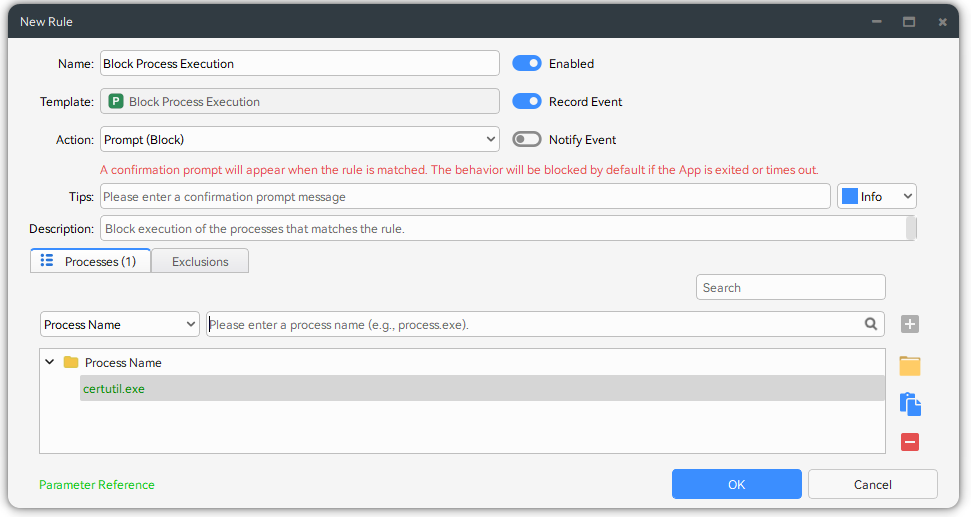
You can select the appropriate response action based on your needs, such as Block or Prompt.
Advanced Rule
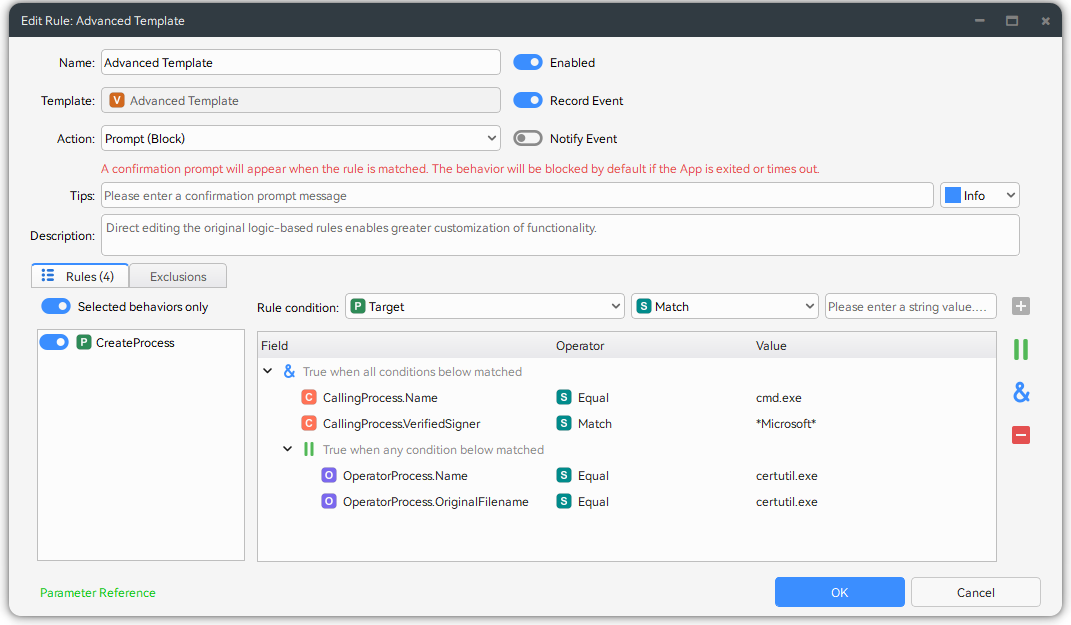
While most rule templates are designed for simplicity and need just a handful of parameters, complex cases demand a more powerful solution. The Advanced Template meets this need by offering full flexibility to combine any conditions and logic.
The following example demonstrates how to create a multi-field combination rule using AND/OR operators.
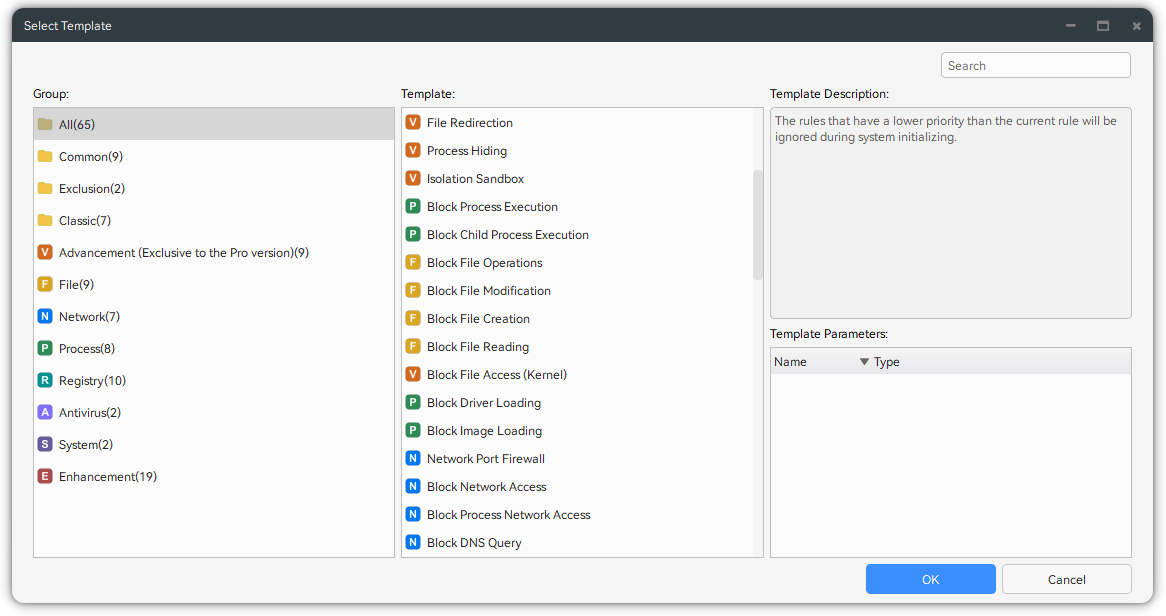
Rule Templates & Built-in Rules
iDefender provides numerous rule templates for quick setup in various situations. It also includes built-in rules, so average users get basic protection immediately without adding any rules themselves. We are constantly improving these rules. If you need protection for a specific case, please let us know.
Prompt Dialog
The prompt dialog is the most important interaction within iDefender. Handling prompts correctly can reduce frequent pop-ups.
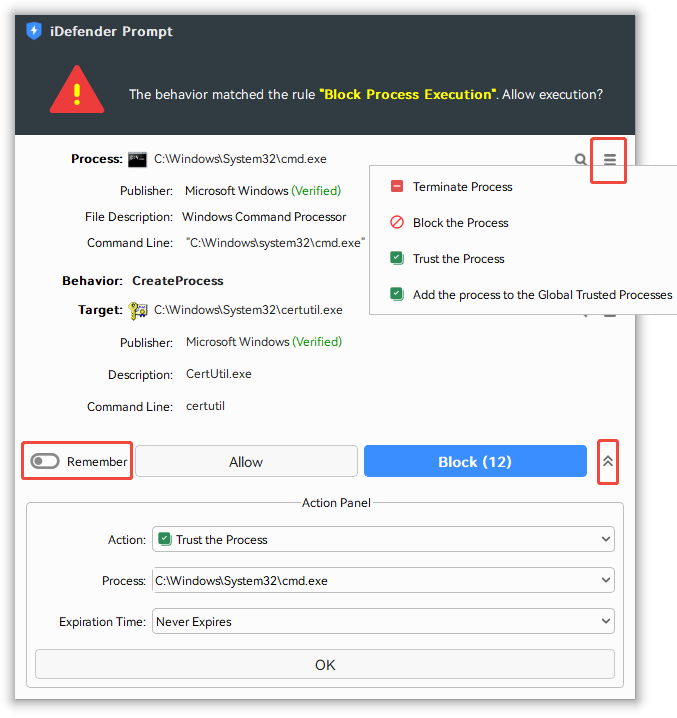
On the prompt dialog interface, both the process and the target have a menu in the upper-right corner, offering the options to Block or Trust. If the process is trustworthy, it is generally advisable to select Trust the Process.
To trust a specific combination of the process and the target, check the Remember box and then click Allow. For more advanced actions, such as trusting the entire process directory or granting temporary trust, please open the Action Panel, which provides extended management capabilities.
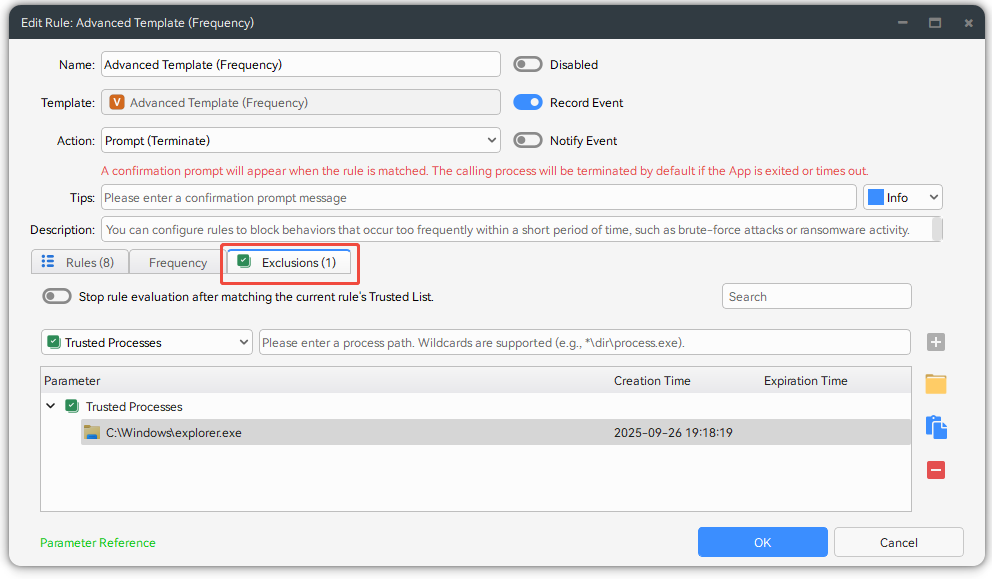
The actions remembered are stored in the Exclusions of the rule.